Virus Y Antivirus Informaticos Tipos Y Clasificaciones
- Virus Y Antivirus Informaticos Tipos Y Clasificaciones Para
- Virus Y Antivirus Informaticos Tipos Y Clasificaciones Puerto Rico
- Virus Y Antivirus Informaticos Tipos Y Clasificaciones En
SoftwareLab.org is operated by Momento Ventures Inc. All rights reserved.Disclaimer: SoftwareLab.org is not an antivirus, VPN or hosting service provider and does not endorse the use of the products featured on this website for unlawful means. It is the responsibility of the user to adhere to all applicable laws. We have no control over the third-party websites we link to and they are governed by their own terms and conditions. SoftwareLab.org is supported by advertisement in order to be a free-to-use resource. We strive to keep the information accurate and up-to-date, but cannot guarantee that it is always the case.
Most of the threats that ESET security products are designed to defend against can be classified as viruses, malware, or remote attacks. Aside from the programs you install on your computer, your computer can be attacked by malicious programs (malware), or even subject to attack over a network by someone operating a computer from a remote location. Malicious software and remote attacks can cause emotional loss, cost you time, and lead to financial loss as well. Below you'll find descriptions of some of the most common types of computer threats, click the links below to jump to the corresponding section. VirusesA Virus is a program that is activated by attaching copies of itself to executable objects.
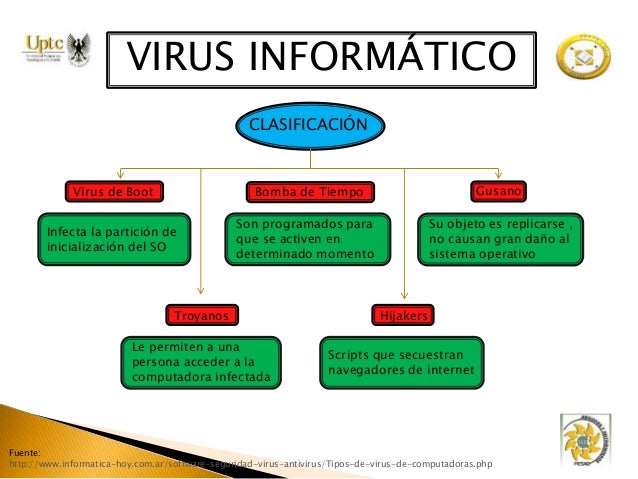
Viruses can reach your computer from other infected computers, via data medium (CD, DVD, etc.) or through a network (local or Internet). There are several types of viruses:File viruses: File-infecting viruses attack executable programs, such as all files with “.exe” and “.com” extensions.Script viruses: Script viruses are a subset of file viruses, written in a variety of script languages (VBS, JavaScript, BAT, PHP, etc.). They either infect other scripts ( for example, Windows or Linux command and service files), or form a part of multi-component viruses. Script viruses are able to infect other file formats, such as HTML, if the file format allows the execution of scripts.Boot viruses: Boot viruses attack boot sectors (removable media boot sector or hard disk master boot sector) and set their own loading routines at start-upMacro viruses: Macro viruses attack documents where other commands (macros) can be inserted. These viruses are often embedded within word processing or spreadsheet applications, since macros are easily inserted into these types of files.Viruses can also be classified according to the way they perform their action. While direct action viruses perform an action immediately after the infected object is activated, resident viruses stay and work in the computer’s memory.MalwareMalware is the term used the describe malicious programs and techniques that are not viruses but still pose a threat to your system.Worm: A worm is an independent program that copies itself across a network.
Unlike a virus (which needs the infected file to be copied in order to replicate itself), the worm spreads actively by sending copies of itself via LAN or Internet, email communication, or through operating system security bugs.They can also bring with them additional malware (such as installing –see below), though this behavior is not strictly limited to worms. Worms can cause a great deal of damage–often they are used to “jam” communication channels by means of a DoS attack. A worm is capable of spreading worldwide, via the Internet, in minutes.Trojan: A Trojan is a malware program that, unlike viruses or worms, cannot copy itself and infect files.
It is usually found in the form of an executable file (.exe,.com) and does not contain anything aside from the Trojan code itself. For this reason, the only solution is to delete it.Trojans have various functions, from keylogging (they log and transmit every keystroke), to deleting files or disc formatting. Some contain a special feature that installs a backdoor program, (a client-server application that grants the developer remote access to your computer). Unlike common (legitimate) software with similar functions, it installs itself without the consent of the client computer.Adware: Adware is short for advertising-supported software, which is software dedicated to displaying advertisements. Adware works by displaying pop-up windows during Internet browsing, by setting various websites as your homepage or by opening a special program interface window.Adware is often bundled with free-to-download programs, and the client is usually informed of this in the End User License Agreement.
Virus Y Antivirus Informaticos Tipos Y Clasificaciones Para
Adware advertisements allow freeware developers to earn revenue by offering program features available only with the paid version. In most cases, installation of adware falls within legal guidelines–there are many legitimate advertising-supported programs. However, issues such as the assertiveness of advertisements as well as their content can make the legality of some adware questionable.Spyware: Spyware is software that uses the Internet for collecting various pieces of sensitive information about the user without his/her awareness. Some Spyware programs search for information such as currently installed applications and a history of visited websites.
Other Spyware programs are created with a far more dangerous aim: the collection of financial or personal data for the purpose of Identity Theft.Riskware: This type of malware includes all applications that increase the user’s security risk when running. As with spyware and adware installation, riskware installation may be confirmed by license agreement. “Dialers” are a common example of Riskware–programs that divert connection to a preset paid number.

Such programs can be legally used for Internet service payments, but they are often misused and the diverting occurs without the user’s awareness.Dangerous applications: A dangerous application is the term used for legal programs that, though installed by the user, may subject him/her to security risks. Examples include commercial keylogging or screen capture, remote access tools, password-cracking and security testing programs.Hoaxes: A hoax is deliberate misinformation sent by email and spread with the help of an unsuspecting or uninformed public. Hoaxes are typically designed to get a user to do something they should not do. Malicious hoaxes often advise users to delete valid operating system files, claiming that the file is a dangerous virus.In many cases, hoaxes refer to a credible institution/company in order to gain the reader’s attention. For example, “Microsoft warns that” or “CNN announced”. These messages often warn of disastrous or even catastrophic consequences.
The warnings have one thing in common – they urge users to send the messages to everyone they know, which perpetuates the life-cycle of the hoax. 99.9% of these types of messages are hoaxes.Hoaxes cannot spread by themselves, the only way to protect yourself is to verify the authenticity of an email message's claims before taking any action.Scams: Broadly defined, scams are deceptions perpetrated on computer users for the purpose of financial gain or identify theft. One of the most common scams involves an unsolicited fax, email, or letter from Nigeria or other West-African nation. The letter will appear to be a legitimate business proposal, but will require an advanced fee from the target. The proposal is of course fraudulent, and any fees paid by the target are immediately stolen.Another common form of scamming includes phishing email messages and websites.
The purpose of these scams is to gain access to sensitive data such as bank account numbers, PIN codes, etc. Access is usually achieved by sending email masquerading as a trustworthy person or business (financial institution, insurance company).The email (or website that the user is directed to) can look very genuine and will contain graphics and content that may have originally come from the source that it is impersonating.
The user will be asked to enter personal data such as bank account numbers or usernames and passwords. All such data, if submitted, can easily be stolen and misused.It should be noted that banks, insurance companies, and other legitimate companies will never request usernames and passwords in an unsolicited email.
For more information on hoaxes, scamming, and phishing,.Remote attacksSpecial techniques which allow attackers to compromise remote systems. These are divided into several categories:DoS attacks: DoS, or Denial of Service, is an attempt to make a computer or network unavailable for its intended users. DoS attacks obstruct communications between affected users, preventing them from continuing in a functional way. One common method of attack involves saturating the target machine with external communications requests, so that the target machine cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable. Such attacks usually lead to a server overload.
Computers exposed to DoS attacks usually need to be restarted in order to work properly.The targets of DoS attacks are web servers and the aim is to make them unavailable to users for a certain period of time.DNS Poisoning: Using DNS (Domain Name Server) poisoning, hackers can trick the DNS server of any computer into believing that fake data is legitimate and authentic. The fake information is cached for a certain period of time, allowing attackers to rewrite DNS replies of IP addresses. As a result, users trying to access DNS poisoned websites will download computer viruses or worms instead of the website's original content.Port scanning: Port scanning is used to determine which computer ports are open on a network host. A port scanner is software designed to find such ports.A computer port is a virtual point which handles incoming and outgoing data – this is crucial from a security point of view. In a large network, the information gathered by port scanners may help to identify potential vulnerabilities.
Such use is legitimate.Still, port scanning is often used by hackers attempting to compromise security. Their first step is to send packets to each port.
Virus Y Antivirus Informaticos Tipos Y Clasificaciones Puerto Rico
Depending on the response type, it is possible to determine which ports are in use. The scanning itself causes no damage, but be aware that this activity can reveal potential vulnerabilities and allow attackers to take control of remote computers.Network administrators are advised to block all unused ports and protect those that are in use from unauthorized access.TCP desynchronization: TCP desynchronization is a technique used in TCP Hijacking attacks.
It is triggered by a process in which the sequential number in incoming packets differs from the expected sequential number. Packets with an unexpected sequential number are dismissed (or saved in buffer storage if they are present in the current communication window).In desynchronization, both communication endpoints dismiss received packets, at which point remote attackers are able to infiltrate and supply packets with a correct sequential number. The attackers can even manipulate or modify communication.TCP Hijacking attacks aim to interrupt server-client and/or peer-to-peer communications. Many attacks can be avoided by using authentication for each TCP segment. It is also advised to use the recommended configurations for your network devices.SMB Relay: SMBRelay and SMBRelay2 are special programs that are capable of carrying out attacks against remote computers.
The programs take advantage of the Server Message Block file sharing protocol which is layered into NetBIOS. A user sharing any folder or directory within the LAN most likely uses this file sharing protocol. Within local network communication, password hashes are exchanged.SMBRelay receives a connection on UDP port 139 and 445, relays the packets exchanged by the client and server, and modifies them. After connecting and authenticating, the client is disconnected. SMBRelay creates a new virtual IP address.
Virus Y Antivirus Informaticos Tipos Y Clasificaciones En

The new address can be accessed using the command “net use 192.168.1.1“. The address can then be used by any of the Windows networking functions. SMBRelay relays SMB protocol communication except for negotiation and authentication. Remote attackers can use the IP address as long as the client computer is connected.SMBRelay2 works on the same principle as SMBRelay, except it uses NetBIOS names rather than IP addresses. Both can carry out “man-in-the- middle” attacks. These attacks allow remote attackers to read, insert and modify messages exchanged between two communication endpoints without being noticed. Computers exposed to such attacks often stop responding or restart unexpectedly.
To avoid attacks we recommend that you use authentication passwords or keys.ICMP attacks: ICMP (Internet Control Message Protocol) is a popular and widely-used Internet protocol. It is used primarily by networked computers to send various error messages.Remote attackers attempt to exploit the weaknesses of ICMP protocol. ICMP protocol is designed for one-way communication requiring no authentication. This enables remote attackers to trigger DoS (Denial of Service) attacks, or attacks which give unauthorized individuals access to incoming and outgoing packets.Typical examples of an ICMP attack are ping flood, ICMPECHO flood and smurf attacks.
Computers exposed to an ICMP attack will experience significantly slower performance in applications that use the Internet and have problems connecting to the Internet.To learn more about threats, remote attacks and malware,.